- URSP Flow in a 5G Network - September 25, 2024
- Cell Broadcast Service or Public Warning System in 5G - July 10, 2020
- 5G Security (5G AKA Authentication) - January 20, 2020
Introduction
In 5G in order to protect UE permanent Identity (SUPI- Subscription Permanent Identifier ) UE never transmit SUPI as it is. UE conceal(encrypt) SUPI using encryption scheme to create SUCI(Subscription Concealed Identifier), before sending it to core network.
Concealing can be done in USIM or ME(Mobile Equipment) depending on the indication configured in USIM by operator. If no indicator present, ME does the concealing.
In core network only UDM has authority to de-conceal the SUCI.
Identity flow between UE and Network

Decoding of SUCI
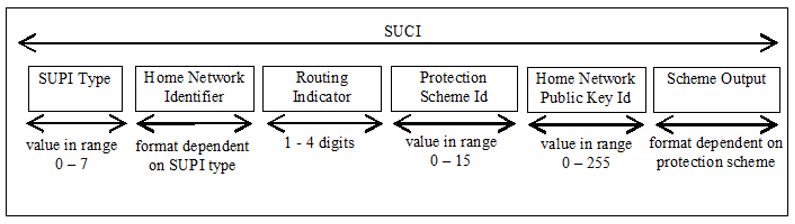
SUPI Type: consisting in a value in the range 0 to 7. It identifies the type of the SUPI concealed in the SUCI. The following values are defined
– 0: IMSI
– 1: Network Specific Identifier
– 2 to 7: spare values for future use.
Home Network Identifier: identifying the home network of the subscriber.
When the SUPI Type is an IMSI, the Home Network Identifier is composed of two parts:
– Mobile Country Code (MCC), consisting of three decimal digits.
– Mobile Network Code (MNC), consisting of two or three decimal digits.
When the SUPI type is a Network Specific Identifier, the Home Network Identifier consists of a string of characters with a variable length representing a domain name. Ex. abc@xyz.com
Routing Indicator: consisting of 1 to 4 decimal digits assigned by the home network operator and provisioned in the USIM.
Routing Indicator: consisting of 1 to 4 decimal digits assigned by the home network operator and provisioned in the USIM.
Protection Scheme Identifier: consisting in a value in the range of 0 to 15 and represented in 4 bits.
- null-scheme 0x0;
- Profile <A> 0x1;
- Profile <B> 0x2.
Home Network Public Key Identifier: consisting in a value in the range 0 to 255. It represents a public key provisioned by the HPLMN and it is used to identify the key used for SUPI protection. In case of null-scheme being used, this data field shall be set to the value 0;
Scheme Output: consisting of a string of characters with a variable length or hexadecimal digits, dependent on the used protection scheme.
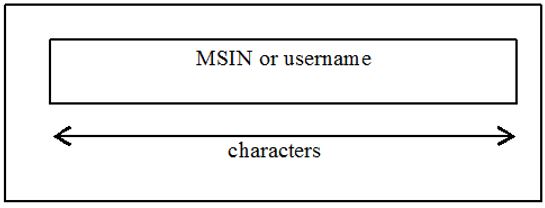
- Null Scheme – For null scheme no encryption happens and scheme output field is replaced by MSIN(value after taking out MCC and MNC from IMSI) value of IMSI as it is.
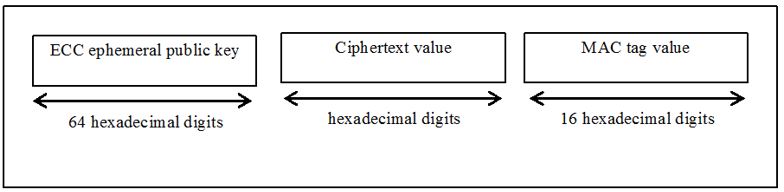
- Elliptic Curve Integrated Encryption Scheme(ECIES) Profile A – In this case scheme out put is further divided in two parts:
- ECC ephemeral public key 64 bits, freshly generated using the provisioned ECIES input parameters.
- Ciphered Text, is of variable length
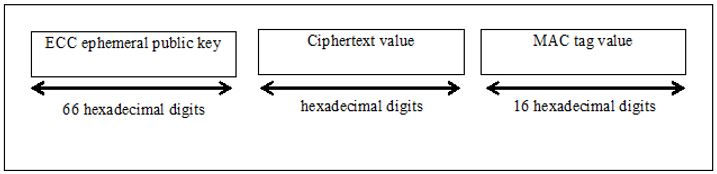
- Elliptic Curve Integrated Encryption Scheme(ECIES) Profile B – In this case scheme out put is further divided in two parts
- ECC ephemeral public key 66 bits, freshly generated using the provisioned ECIES input parameters.
- Ciphered Text, is of variable length
Note: Detailed into Elliptic Curve Integrated Encryption Scheme(ECIES) will be discussed in another Blog.
11 Comments