- URSP Flow in a 5G Network - September 25, 2024
- Cell Broadcast Service or Public Warning System in 5G - July 10, 2020
- 5G Security (5G AKA Authentication) - January 20, 2020
5G Security Procedure between UE and Network
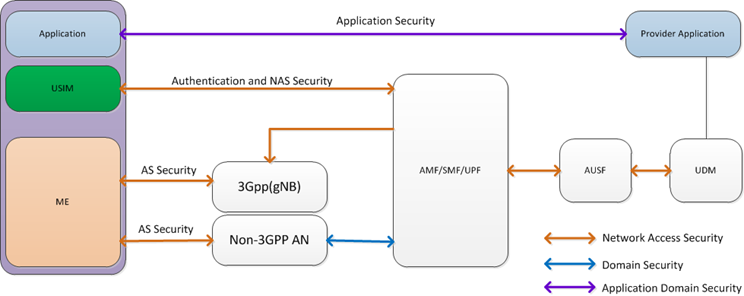
Security Types in 5G Network
- Security required for UE to access network services comes under Network access security. This security mainly cover Authentication, Integrity and ciphering of Signalling and data.
- Domain Security mainly covers secure communication between different Network nodes.
- Application domain security covers security mechanism between peer applications.
- There are two different kind of authentication
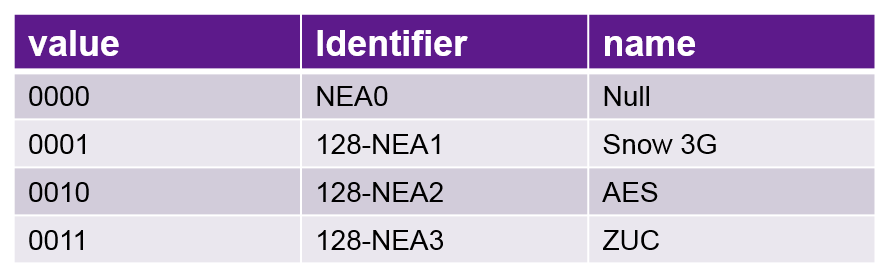
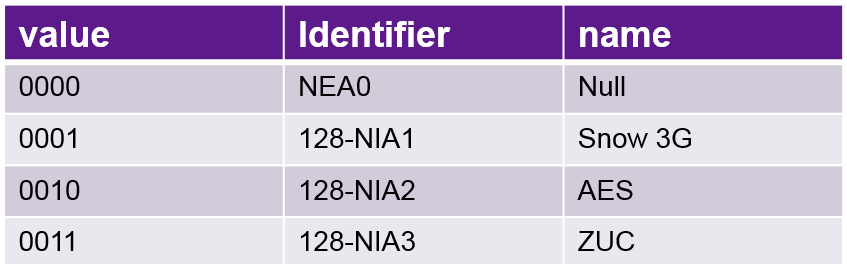
Different Authentication, Ciphering and Integrity Algorithms
- In most cases for Authentication Key Agreement(AKA), operators use Milenage/TUAK algorithm. But some cases proprietary algorithm.
- For Cyphering and Integrity Protection following Algorithms are used.
Ciphering Algorithms
Integrity Algorithms
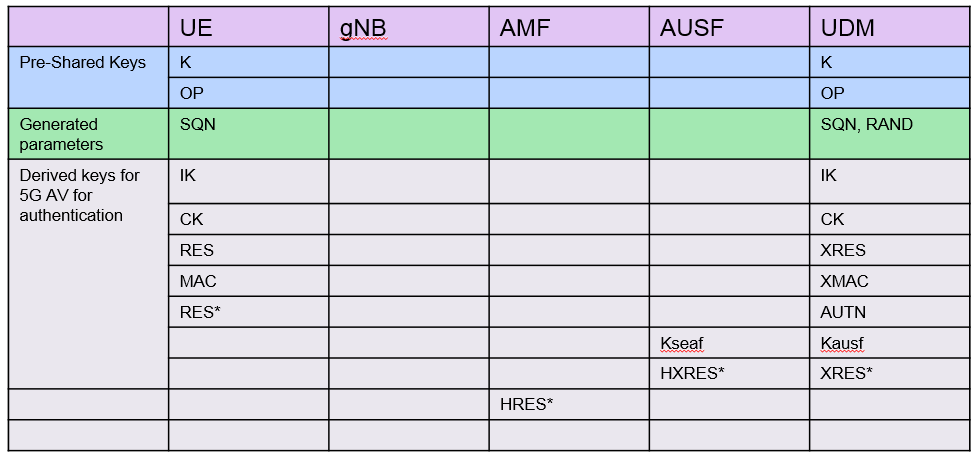
Key Distribution
5G AKA Authentication Procedure
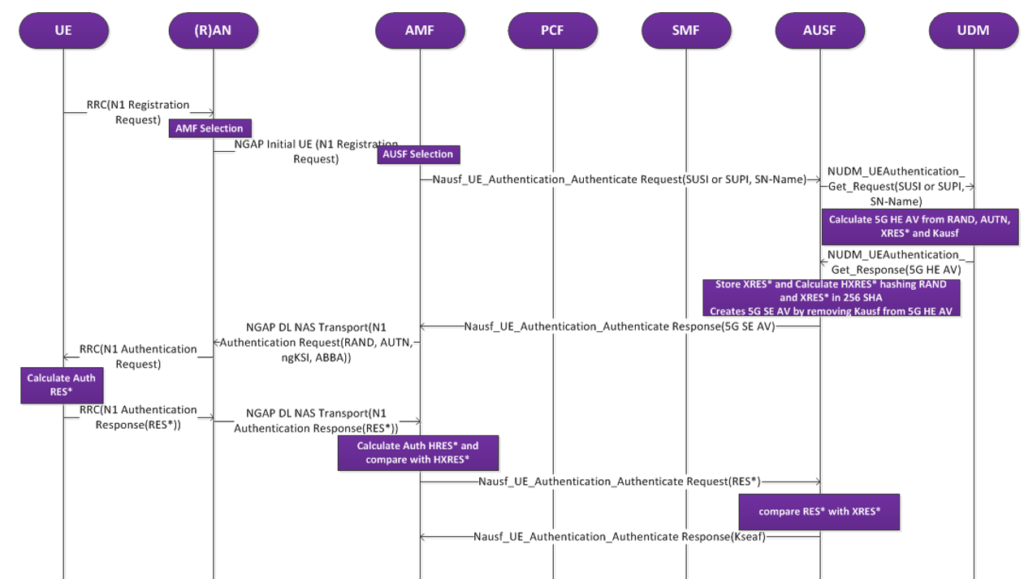
Authentication Flow Steps
- After receiving Registration Request, AMF initiates authentication procedure with UE, if UE security context is not existing with AMF.
- AMF sends Nausf_UEAuthentications Request with SUCI or SUPI and Serving network name.
- AUSF based on the Serving Network name, determine if AMF is authorised to send this message.
- Then AUSF, sends Nudm_UEAuthentication_Get Request with SUPI/SUCI to UDM.
- UDM Calculates the 5G HE AV as below. UDM Uses Milenage functions to derive MAC, XRES, CK, IK and AK.

- UDM derives Kausf is as follows using HMAC-SHA-256(K, S) KDF(Key Derivation Function) function as below.

- UDM derives XRES* as follows using HMAC-SHA-256(K, S) KDF function.
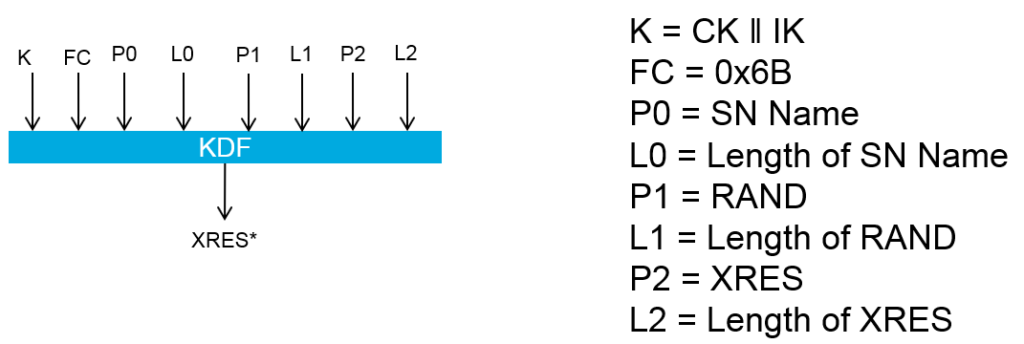
- UDM derives 5G HE AV from above derived keys as below and send it to AUSF with message “Nudm_Authentication get Response” 5G HE AV = RAND ‖ XRES* ‖ Kausf ‖ AUTN
- Derivation of 5G SE AV at AUSF
- HXRES* Calculation at AUSF: HXRES* is 128 bit MSB of the output of SHA-256 hash, calculated by passing RAND || XRES* as input to SHA-256 algorithm.

- AUSF derives Kseaf from Kausf by passing K= Kausf and S = 0x6C || Serving Network Name || Lenth of Serving Network Name to KDF function.

- AUSF calculates 5G AV and 5G SE AV as below and send 5G SE AV to AMF. 5G AV = RAND ‖ HXRES* ‖ Kseaf ‖ AUTN 5G SE AV = RAND ‖ HXRES* ‖ AUTN
- AMF Sends NAS Authentication Request to UE with RAND and AUTN from 5G SE AV.
- UE Uses Milenage functions to derive XMAC, RES, CK, IK as below.

- UE Verify the MAC received in AUTN with XMAC calculated above to authenticate the network and check the freshness of AUTN. Here if the comparison fails then it will send authentication failure with AUTS.
- UE derives RES* as follows using HMAC-SHA-256(K, S) KDF function. using keys calculated above, and then sends RES* to AMF.
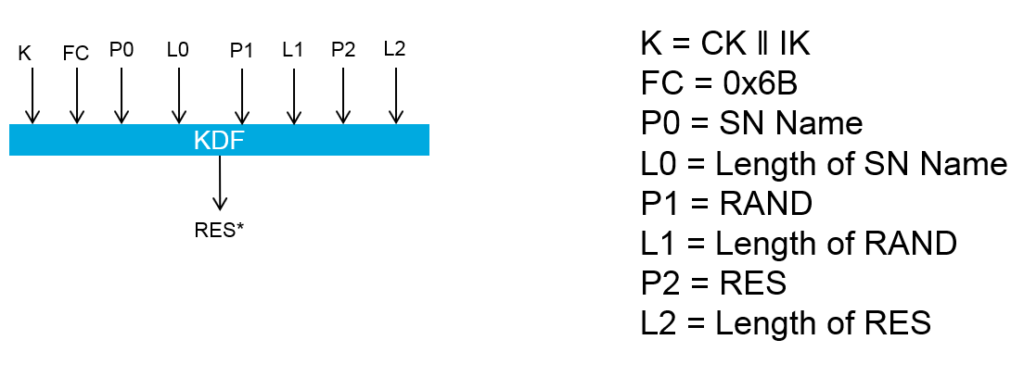
- AMF Calculates HRES* from RES* : HRES* is 128 bit MSB of the output of SHA-256 hash, calculated by passing RAND || RES* as input to SHA-256 algorithm.

- AMF compares HRES*(Calculated above) with HXRES* received from AUSF to check for successful authentication.
- AMF sends RES* received from UE to AUSF with “Authenticate Request” message.
- AUSF compares RES* with the XRES*(part of 5G HE AV) received from UDM in step 5.
- If Comparison is successful, AUSF sends Authentication Event notification to UDM with “Success”.
5 Comments